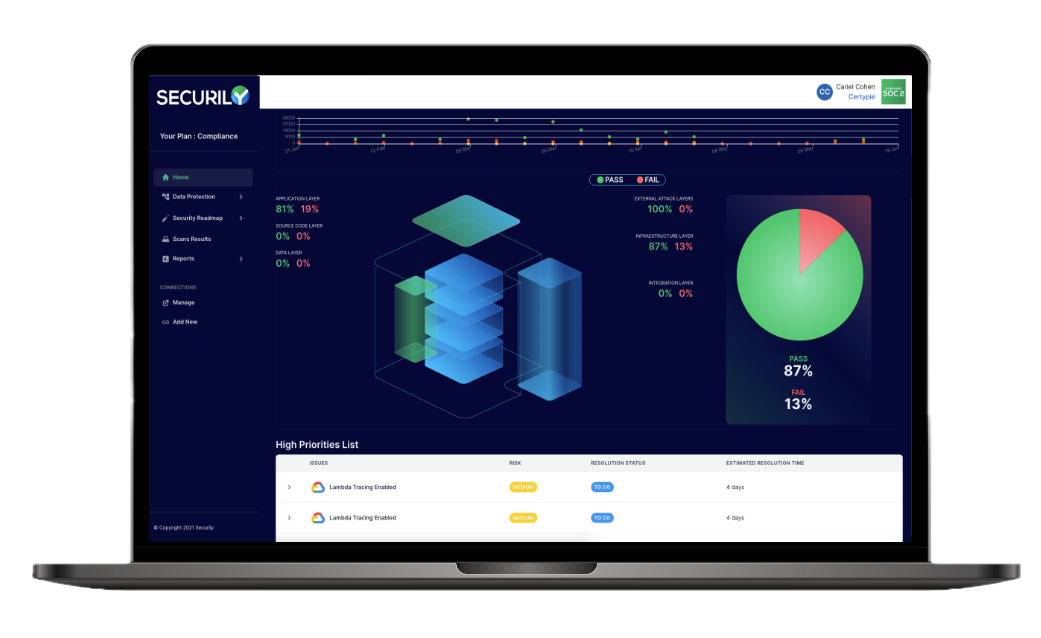
Penetration Testing
Powered by AI
Identify and mitigate security vulnerabilities in your organization's computer systems, networks, and applications with the help of our experienced team of pentesting professionals.
GET IT DONE
We are ENABLING our customers to close deals with...